In June this year,
Cybereason
published a
blog post
on Operation Soft Cell, a targeted attack against telecom providers around the world. The actors behind the operation are particularly interested in Call Detail Records (CDR) for specific high-value users, which give them valuable metadata on their communication and location. Prior to publishing their blog post,
Cybereason
researchers Mor Levi, Amit Serper and Assaf Dahan had submitted their research to VB2019 – and in October, they delivered their paper in London.
Based on the TTPs, which include the use of the Poison Ivy RAT and the China Copper web shell,
Cybereason
had concluded that the actors were likely Chinese. In a
blog post
published this week,
Microsoft
raises awareness for this actor, which it labels ‘GALLIUM’.
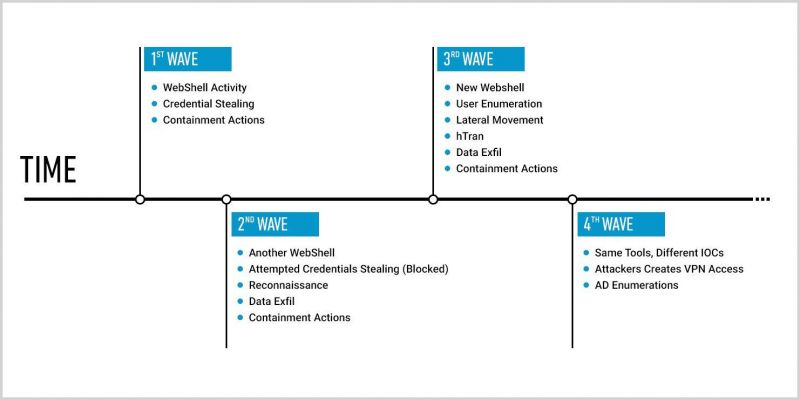
Changes and new activity every quarter.
Today, we publish the VB2019 paper by
Cybereason
researchers Mor Levi, Amit Serper and Assaf Dahan in both
HTML
and
PDF
format.

Leave a Reply