OpSec mistakes are what lead to many malware discoveries, but in the case of the Geost
Android
botnet the mistake was a really interesting one: its operators were using another botnet, HtBot, to manage infected devices, not realising that researchers were analysing some HtBot-infected hosts.
This led researchers Sebastian García, Maria Jose Erquiaga and Anna Shirokova to the discovery of Geost, a large
Android
botnet mostly targeting users of online banking in Russia.
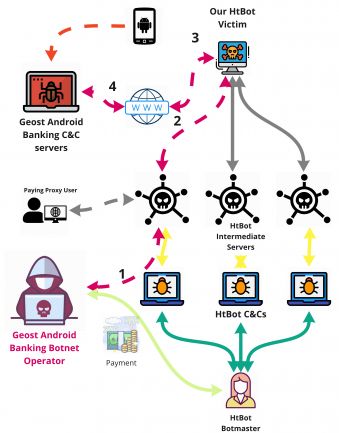
Discovery of the Geost botnet. A monitored bot of the HtBot malware was used by the Geost botmasters. First, the Geost botmaster connected to the HtBot network; second, the HtBot network relayed the data to our bot; third, our bot sent the traffic to the Internet; fourth, the botmaster accessed the Geost C&C server on the Internet.
Today we publish the researchers’ paper on Geost in both
HTML
and
PDF
format. We have also uploaded the video of Sebastian and Anna presenting at VB2019 in London to our
YouTube
channel.

Geost botnet. The story of the discovery of a new Android banking trojan from an OpSec error
Read the paper (HTML)
Download the paper (PDF)
Leave a Reply