Clicking on links leads to Blackhole rather than phishing site.
Fake
PayPal
receipts were being spammed out this morning, with links leading to a version of the Blackhole exploit kit.
The emails look like typical
PayPal
confirmation emails and suggest that funds have been sent from the user’s account. The supposed recipient of these funds varies between the emails, but they all share the surname ‘Peterson’. Of course, the links in the email don’t send the user to
PayPal
‘s website, but instead link to a landing page on a compromised website.
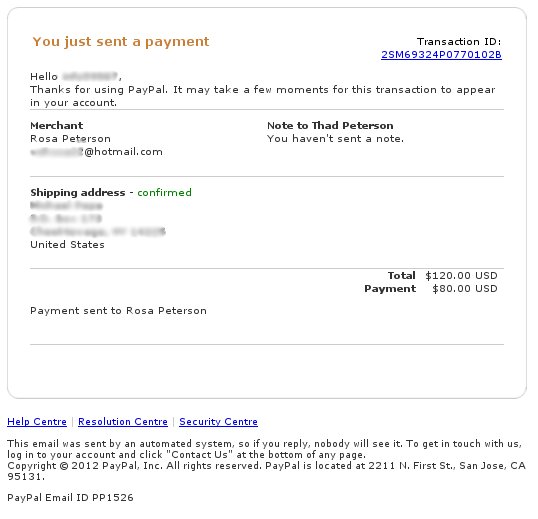
This landing page is an otherwise empty HTML page, where three pieces of JavaScript code are being loaded from three external websites. These three sites have been compromised as well, and each script contains the same piece of code that merely redirects the browser to another site. The use of three pieces of the same code means that the redirect will continue to work even if one or two of the sites are taken down or cleaned up.
The website the user is sent to appears to be run by the cybercriminals behind the attack themselves; it connects directly to the IP address and does not use a domain name. The page contains a piece of obfuscated JavaScript. De-obfuscating this code showed that this is, in fact, the infamous Blackhole exploit kit, which attempts to install malware on a user’s machine via a number of known vulnerabilities in browser add-ons such as
Flash
and
Java
, as well as in the
Windows
operating system itself.
It may seem surprising that the criminals chose to send the user to an exploit kit, rather than to a phishing site. However, as many users are aware of phishing scams, even if they had clicked the link in the email, the domain name would be an obvious sign that something was not right. On the other hand, exploit kits silently infect the unprotected user which, via pay-per-install affiliate schemes, could generate money for those sending the spam.
Virus Bulletin has alerted the ISP that hosts the website running the exploit kit. At time of writing, the site is no longer accessible.
A technical paper on the Blackhole exploit kit, written by
Sophos
‘s Fraser Howard, can be found
here
.
iSIGHT
‘s Ken Dunham and Shane Hartman will present a paper ‘
Blackhole exploit kit dominates the market
‘ at VB2012 in Dallas (26-28 September). Registration for VB2012 is now
open
.
Posted on 2 May 2012 by
Virus Bulletin
Leave a Reply