Visitors to child abuse websites likely target of operation, but will there be collateral damage?
A zero-day exploit in
Firefox 17
that was probably used to track the visitors to child abuse websites hosted on the
Tor
network will spark further debate on the notion of “good malware” and could lead to very serious false positives.
Tor
is software for online anonymity – it uses encrypted connections routed via a number of nodes to effectievly hide the user’s real location. It can be used both to bypass censorship and to access a service without giving details about one’s real location.
Tor Hidden Services
takes this concept one step further: here, the service itself is also hidden by the
Tor
network and its real location cannot be discovered.
Tor Hidden Services
, which uses the pseudo top-level domain
.onion
, is used for instance by
The New Yorker
in its
Strongbox
service, where informers can share data with the magazine anonymously. Perhaps unsurprisingly, the
Tor
service is also popular in the darker echelons of the web. ‘The Silk Road’, a black market only accessible through
Tor
, made the news recently when it was used to
send heroin
to security blogger Brian Krebs in an attempt to incriminate him. A number of sites for sharing child abuse images are also known to be hosted on
Tor
.
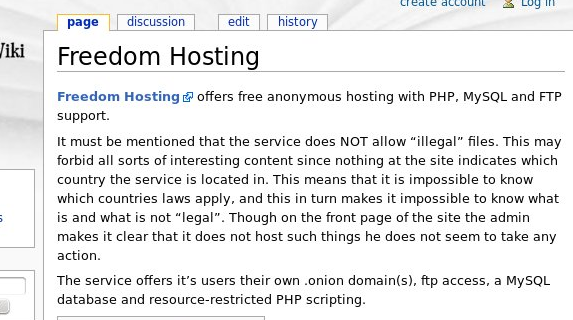
Description of ‘Freedom Hosting’ on ‘The Hidden Wiki’, itself a Tor Hidden Service
.
Of course, even sites hosted on
Tor Hidden Services
have a real location, and it is believed that many sites were hosted at
Freedom Hosting
– a hosting service that was known to turn a blind eye to illegal activities on its network.
Freedom Hosting
is believed to have been run by Eric Eoin Marques, a 28-year-old with dual Irish-American citizenship, who was
arrested
in Ireland over the weekend and described as the “largest child-porn dealer on the planet”.
At the same time, sites hosted at
Freedom Hosting
are believed to have been serving a zero-day exploit for
Firefox 17
. While not the latest version of the popular browser, it is what the
Tor Browser bundle
is based on. The
Tor Browser bundle
is probably the easiest way to access
Tor Hidden Services
and will have been used by many of those visiting the sites.
The exploit did no more than send the user’s real IP address to a server in the United States – which makes it likely that it was run by a law enforcement agency. Given the comments made by the FBI regarding Marques’ arrest, it is likely that the operation targeted those visiting child abuse websites.
The anti-malware community has always been pretty univocal on the use of malware for “good” purposes – which is something that, if not morally wrong, is at least considered something security solutions should still protect against. Of course, there are many who will not be at all displeased at the idea of this exploit leading to the arrest of people who helped enable child abuse.
But things are a little more complicated than that. Not all
Tor
services hosted at
Freedom Hosting
were illegal.
Tor Mail
, an anonymous email service, is also believed to have been hosted at
Freedom Hosting
; indeed, it has been down since the weekend. From the analysis seen online, it appears that the exploit does not include details on which particular services were accessed by the user.
It would not be a good thing if the anonymity of those accessing legal services hosted on the
Tor
network were breached. But it would be seriously wrong if those people were thrown on the same pile as those accessing child abuse websites: a false accusation of enabling child abuse can have serious consequences and should be avoided at all costs.
Finally, it is a sad and sobering thought to realise that it is far from clear that this operation will have done anything to help the victims of child abuse.
Brian Krebs has a good summary of what happened on his blog
here
, while the official response from
The Tor Project
– which stresses that it is in no way affiliated with
Freedom Hosting
– can be found
here
.
Posted on 5 August 2013 by
Martijn Grooten
Leave a Reply