‘KnockKnock’ tool made available to the public.
Over the next few months, we will be sharing VB2014 conference papers as well as video recordings of the presentations. Today, we have added ‘Methods of malware persistence on Mac OS X’ by Synack researcher Patrick Wardle.
It has been a while since
Apple
used the scarcity of
Mac
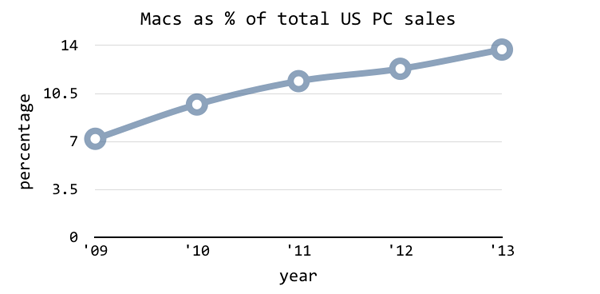
viruses as part of its marketing strategy. Malware targeting
OS X
is fairly common these days, and it is likely to be here to stay.
In his presentation (which we
previewed
on our blog two months ago), Patrick Wardle showed various ways in which
Mac
malware manages to persist on a machine it has infected, thus making sure it runs even after a reboot. He also showed how many recent families of
OS X
malware maintained persistence.
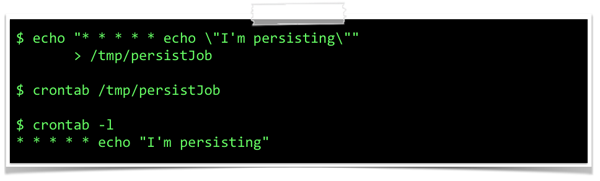
Patrick also demonstrated the
KnockKnock
tool he has created – and made available for free. The tool, which can easily be extended using plug-ins, allows anyone to see persistent binaries that are to be executed automatically at each boot.
You can read Patrick’s paper
here
in HTML-format, or download it
here
as a PDF (no registration or subscription required). You can download the presentation slides
here
. We have also uploaded the presentation to our YouTube channel.
Later this week, we will publish a new paper by Patrick in which he looks at a recently discovered
OS X
malware family.
Posted on 24 October 2014 by
Martijn Grooten
Leave a Reply