Ten talks covering hot research added to the VB2015 programme.
There are just over two weeks to go until more than 400 security professionals descend on Prague for VB2015, the 25th Virus Bulletin International Conference.
With the addition of ten last-minute papers, the conference programme is now almost complete: two keynotes (by
Ross Anderson
and
Costin Raiu
), seven ‘Small Talks’ and 51 regular presentations mean the three conference days are packed with interesting talks and discussions on a range of relevant topics that are important to the security community.
Targeted attacks
Unsurprisingly, some of the last-minute talks deal with recently analysed targeted attacks.
Kaspersky
‘s Kurt Baumgartner will
present research
into the Turla malware, which used hijacked satellite communications for command and control.
Meanwhile,
Microsoft
researchers Jeong Wook Oh and Elia Florio will
talk about
their analysis of a Win32k exploit used by Duqu 2.0, which made the news
earlier this year
when it was found to target a security company.
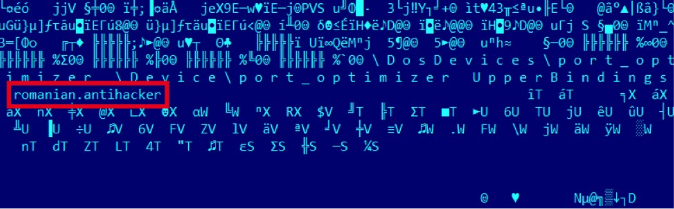
Part of Duqu 2.0 code, with a possible reference to VB2015 keynote speaker Costin Raiu. Source: Kaspersky Lab.
Operation Potao Express is another noteworthy cyber-espionage operation, in this case noteworthy for having served a trojanized version of the popular open-source encryption software
TrueCrypt
for several years.
ESET
researchers Robert Lipovsky and Anton Cherepanov
will present
their research into this campaign. Last year the same researchers talked about how the BlackEnergy trojan was used in targeted attacks in Russia and Poland; their
presentation
was the first to publicly mention what would later become known as the
Sandworm
vulnerability.
Anonymizing VPN services
Not all hot research involves cyber-espionage though. The Bunitu trojan infects
Windows
machines and uses these as proxies:
Sentrant
‘s Sergei Frankoff and
Malwarebytes
‘ hasherezade will present
their research
into this malware as well as describe how access to the proxies is sold as a VPN service.
Non-Windows operating systems
Interestingly though, six of the ten last-minute talks involve non-
Windows
operating systems.
Synack
researcher Patrick Wardle will
talk about
OS X
‘s built-in anti-malware feature
Gatekeeper
and how (in)effective it is against today’s threats.
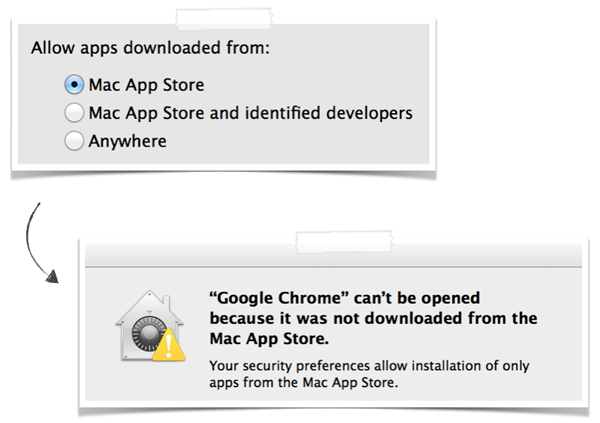
Gatekeeper in action. (From Patrick Wardle’s
VB2014 paper
.)
Two last-minute presentations discuss
Linux
malware; in particular malware targeting various kinds of routers.
ESET
researcher Olivier Bilodeau
will present
the story of Linux/Moose, a piece of router malware that was used, among other things, for ‘like’ and ‘view’ fraud on social media.
The purpose of router threat Linux.Wifatch is less clear, but
Symantec
‘s Mario Ballano will
try to unravel
some of its mysteries.
Android
Finally, three talks deal with the popular
Android
mobile operating system.
Intel
‘s Carlos Castillo
will describe
how he and his colleagues found a group of
Android
malware authors whose Backend-as-a-Service (BaaS) solution was badly implemented, allowing the researchers to gather a lot of information about the C&C protocol as well as the data collected on the server.
While there are a number of ways to install malware on
Android
devices, nothing is as persistent as installing it in the factory.
G Data Software
researcher Alexander Burris spent quite some time looking at smartphones with pre-installed malware, the malware having been installed possibly due to a weakness in the supply chain. Alexander
will present
his research into this issue.
It’s not all bad news though.
Google
‘s Sebastian Porst
will explain
what the company’s
Android
Security Team did to keep users safe from apps that attempted to steal login details at various Russian banks.
VB2015
Registration
for the conference is still open. Don’t forget that if you are a student, you may be
eligible
for an 87% discount — and we also give you the opportunity to present your research in a five-minute ‘Lightning Talk’.
If you’ve already registered, there’s still time to sign up for the traditional
foosball (table football) tournament
, organised by
G Data
. Or, if you’d rather exercise your brain than your wrists, why not submit something for the first round of ‘
Steganoprague
‘, a steganographic puzzle and competition?

Posted on 15 September 2015 by
Martijn Grooten
Leave a Reply