In our research for the
VBWeb
tests, in which we measure the ability of
security products
to block malicious web traffic, we recently noticed some sites hosted on
Google
‘s
Blogspot
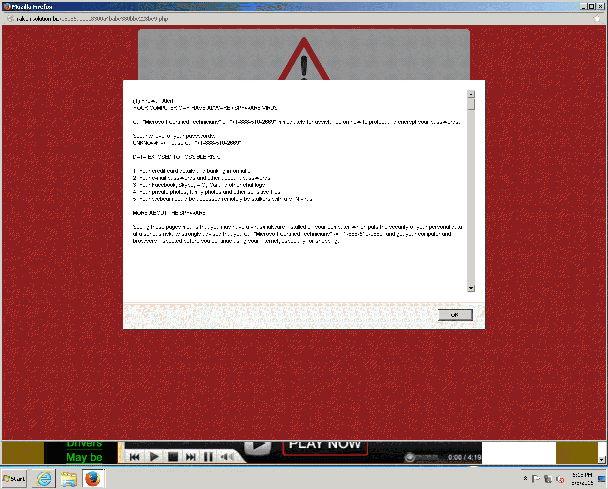
service that presented the user with a warning about a malware error and a telephone number which they were urged to call in order to speak to “Microsoft technicians” about the issue.
Despite ransomware being the most serious (and for cybercriminals most profitable) threat right now, there is still a market for scams that exploit the hardest-to-fix vulnerability: human gullibility.
While support scammers initially took the initiative themselves and telephoned random people, telling them that they had serious (entirely fabricated) computer issues that needed to be fixed, the trend in recent years has been to present the user with a pop-up and make them place the call. In both cases, of course, there is a hefty fee for “fixing” these imaginary problems.
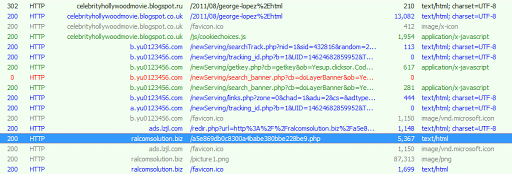
In this case, the sites that served the pop-up were laden with ads, to such a point that the ads literally hid all of the sites’ actual content (celebrity photos) — but a user wouldn’t realise this until they actually visited an affected site. Though the majority of these ads were a mere nuisance, one of the (legitimate) ad providers served the pop-up through a number of redirects.
We have seen similar blogs affected by malvertising that serves exploit kits, which often leads to ransomware — a significantly more serious threat. But security software running on the endpoint does at least have a chance
against ransomware
. Against a gullible user there is no protection.
At VB2014, Malwarebytes researcher
Jérôme Segura
presented a paper on support scams. At VB2016 in Denver, he and his colleague
Chris Boyd
will present a
paper
on malvertising.
Registration
for VB2016 is now open.
This blog was written by Martijn Grooten together with Adrian Luca.
Leave a Reply