Malware infections usually start with a user opening an attachment, visiting a link, or simply accessing an infected site with a vulnerable browser. But once malware has infected an endpoint, it often looks for other devices in order to spread further, or at least to include the files on those devices in its malicious encryption efforts.
Today, we publish a short paper by
Acalvio
researcher Abhishek Singh, who uses examples from recent ransomware samples to show how malware spreads within a network (‘lateral movement’) or even outside the network. You can read the paper either in
HTML
or
PDF
format.
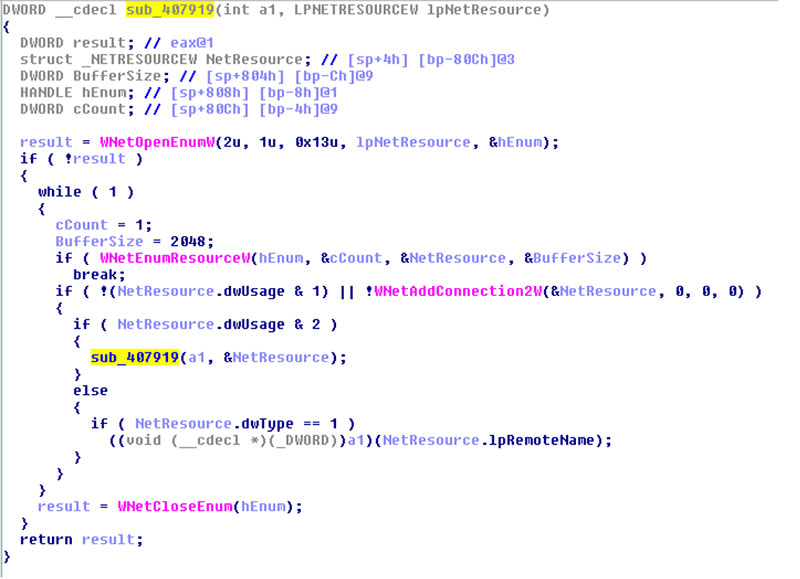
If you like this paper, why not read some of the other papers Abhishek has written for
Virus Bulletin
, such as a
paper
on techniques used by malware to evade automated analysis.
Leave a Reply