Ask a programmer to perform the same task twice and they will write a tool that automates it. Malware analysts are no different, and the Virus Bulletin Conference has a long history of including papers on tools and tricks that make the task of analysing malware a lot easier.
‘Crypton’ is such a tool. It was developed by
F5 Networks
researchers Julia Karpin and Anna Dorfman to speed up the reverse engineering process by decrypting encrypted content found in a (malicious) binary. Given that malware authors tend to take the ‘encrypt everything’ mantra to the extreme, this tool could save a lot of time.
However, the
paper
, which the researchers will present at VB2017, isn’t just about ‘yet another tool’. It actually describes the process Julia and Anna went through in designing and building it. For fellow researchers attending the conference, this is probably even more interesting than the end result.
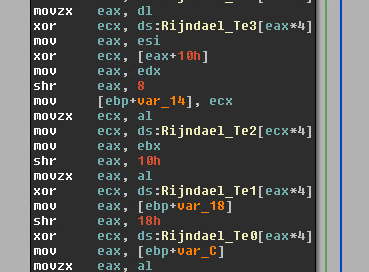
Part of the disassembled code of the AES algorithm, found as such in many a malware sample.
To learn from Julia and Anna’s work, and to see more than 50 other speakers in Madrid next month, don’t forget to
register
for VB2017 – and don’t forget that there are special
discounted tickets
available for students!

Leave a Reply