Seven years ago, the first VB
conference paper
on
Android
malware looked at what was then a new, but growing trend. Since then both the threat and the research community have grown enormously, and every VB conference since has featured several talks on
Android
malware.
VB2018
is no exception.
One of this year’s
Android
talks will by Maddie Stone, a researcher from the developer of
Android
itself,
Google
. Maddie will
present
her analysis of an anti-analysis library used by thousands of malicious APKs to obfuscate their functionality.
The library, named ‘WeddingCake’ because of its many layers, uses techniques also commonly seen in
Windows
malware, from dynamic decryption to attempts to detect being run inside a research environment. Maddie’s analysis demonstrates the challenges faced by those researching the still growing threat of
Android
malware.
For a taste of Maddie’s VB2018 talk and paper, take a look at the slides (
pdf
) of a talk she gave at
Black Hat USA
last week, in which she focused on the same library.
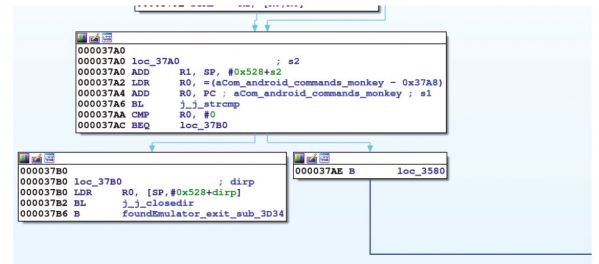
The library checks for the presence of the
Monkey
tool commonly run in emulators.
Don’t forget to
register
for VB2018 to guarantee your place in Montreal, where you will also be able to
Sophos
‘s Rowland Yu
discuss
how to perform network analysis of
Android
malware as well as attend a
workshop
on
Android
malware analysis by
Fortinet
‘s Axelle Apvrille.
And if you yourself have performed some hot research on
Android
malware (or any other security topic), note that the
call for last-minute papers
remains open until 2 September!
Leave a Reply