Any web app that relies on some kind of user input is potentially vulnerable to some kind of command injection, be it MySQL, NoSQL or OS command injection. Indeed, OWASP lists this as one of the topmost security risks.
In a paper presented at VB2019 in London,
Prismo Systems
researchers Abhishek Singh and Ramesh Mani discussed code injection vulnerabilities and presented a tool that could detect this vulnerability class.
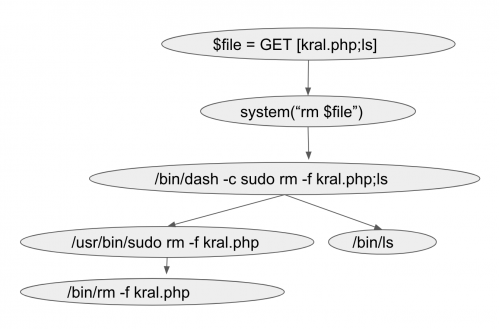
Dynamic call graph with OS command injection exploit.
Today we publish Abhishek and Ramesh’s paper in both
HTML
and
PDF
format. We have also uploaded the recording of their presentation at VB2019 in London to our
YouTube
channel.

Catch me if you can: detection of injection exploitation by validating query and API integrity
Read the paper (HTML)
Download the paper (PDF)
Did you see we have opened the
Call for Papers
for VB2020 in Dublin? Submit your abstract before 15 March for a chance to make it onto the programme of one of the most international threat intelligence conferences!
Leave a Reply