Though active for only a little over a year, GandCrab was one of the most successful ransomware operations and caused a great deal of damage worldwide. Running as a Ransomware-as-a-Service scheme, the malware regularly updated itself to newer versions to stay ahead of decryptors released by security researchers, and regularly included taunts, jokes and references to security organizations and researchers in its code.
One security vendor that found itself firmly in GandCrab’s firing line was South Korea-based
AhnLab
: GandCrab specifically targeted the company and its anti-malware program
V3 Lite
, even revealing a vulnerability in the security program and making attempts to delete it entirely.
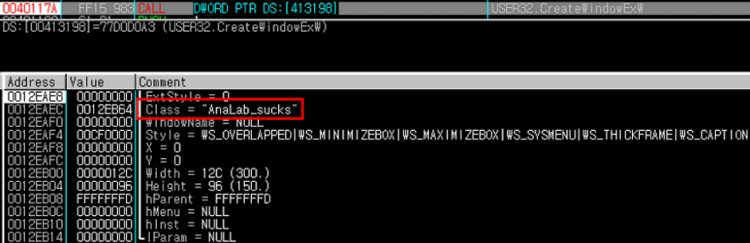
AhnLab text string used as a class name in the malware.
In a new paper (published today in both
HTML
and
PDF
format), the
AhnLab
Security Analysis Team reveal the full details of the battle that went on between GandCrab and
AhnLab
.
For more details of GandCrab, also see the
VB2019 paper
and
presentation
by McAfee researchers John Fokker and Alexandre Mundo, who looked both at the malware code and its evolution, and at the affiliate scheme behind it.

Leave a Reply