In September 2013,
Kaspersky
reported
a new APT group it dubbed ‘Kimsuky’, which it linked to North Korea. The group, whose interests include South Korean industry, journalists and North Korean defectors, continues to be active: recent activity was analysed by
Yoroi
earlier this month
.
Jaeki Kim. Kyoung-Ju Kwak and Min-Chang Jang from
Financial Security Institute
have been tracking the group and its various spear-phishing activities for years. In a paper presented at VB2019 in London, they detailed the tools and activities used by this group, some of which they were able to analyse through OpSec failures by the group.
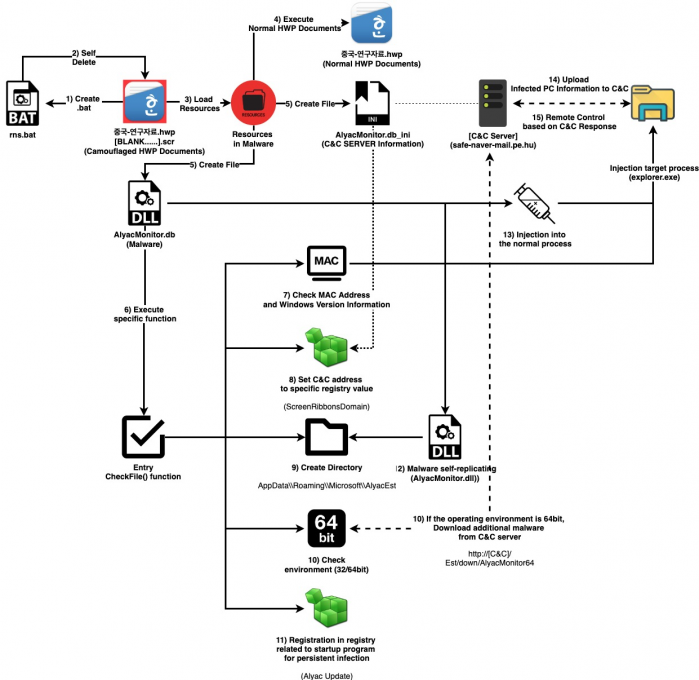
The flow of malware used in spear-phishing attacks.
Today, we publish the researchers’ paper in both
HTML
and
PDF
format.

Kimsuky group: tracking the king of the spear-phishing
Read the paper (HTML)
Download the paper (PDF)
Are you tracking an APT group? Have you fought their targeting of your organisation? Why not
submit a paper
for VB2020 in Dublin, Ireland, the deadline for which is
Sunday 15 March.
Leave a Reply