One of the many highlights of last year’s Virus Bulletin Conference was
a last-minute paper
by
ESET
researchers Anton Cherepanov and Robert Lipovsky on Industroyer, ‘the first ever malware specifically designed to attack power grids’ and which was behind a December 2016 blackout in Ukraine.
This year, the VB2018 conference programme includes a
paper
by
Dragos
researcher Joe Slowik, who performs a thorough analysis of the malware his company dubs ‘CRASHOVERRIDE’.
Joe explains in his paper that, rather than a single piece of malware, CRASHOVERRIDE is best understood as an event with multiple inter-dependent stages. His paper looks at all these stages, thus not only providing a very welcome analysis of one of this decade’s most important malware attacks, but also giving ICS operators and defenders a good idea as to how CRASHOVERRIDE-like attacks can be detected, mitigated and defeated.
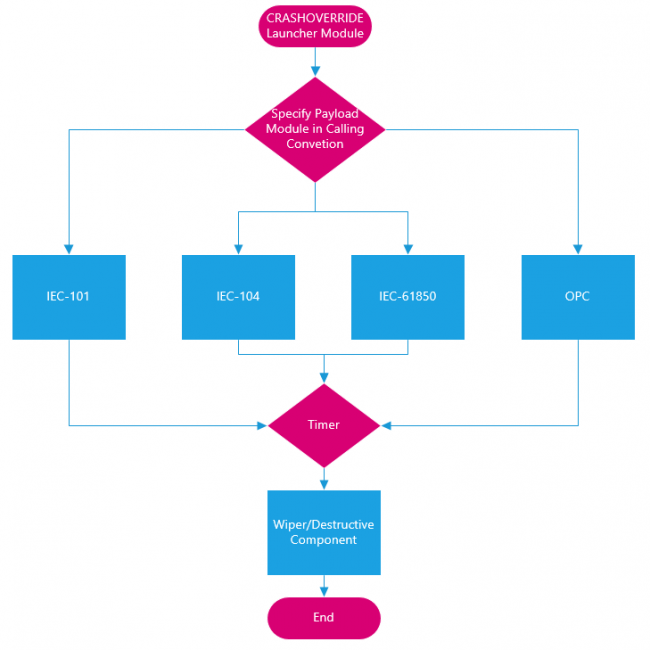
Joe’s paper is among the more than 50 presentations on the
VB2018 programme
, which also includes a paper by the aforementioned Anton Cherepanov, who this year will speak about an
APT attack
taking place in Central Asia.
VB2018
takes place in Montreal next week. It is still possible to
register
!

Leave a Reply