Yesterday, the US Justice Department
brought charges
against an alleged hacker for the North Korean government. The man, Park Jin Hyok, is accused of being connected with the 2014
Sony Pictures Entertainment
hack, as well as the 2017
WannaCry worm
and various hacks of banks through the
SWIFT
system.
Though charges against individuals linked to state-sponsored cyber attacks aren’t new, this is the first time a North Korean individual has been charged by the US government in connection to such attacks. Park is believed to be a member of the Lazarus Group, generally assumed to be behind the mentioned attacks.
Unsurprisingly, given the political situation on the Korean peninsula, the Lazarus Group has also been active in South Korea. At
VB2018
next month, Minseok (Jacky) Cha, a researcher from South Korean security firm
AhnLab
, will present a
paper
which focuses on this activity.
He found evidence of activity linked to the Lazarus Group going back as early as April 2011, as well as various operations by this group in the seven years since, with targets including government institutions, defence contractors and media companies. Minseok provides an overview of these operations and looks at similarities in the malware used.
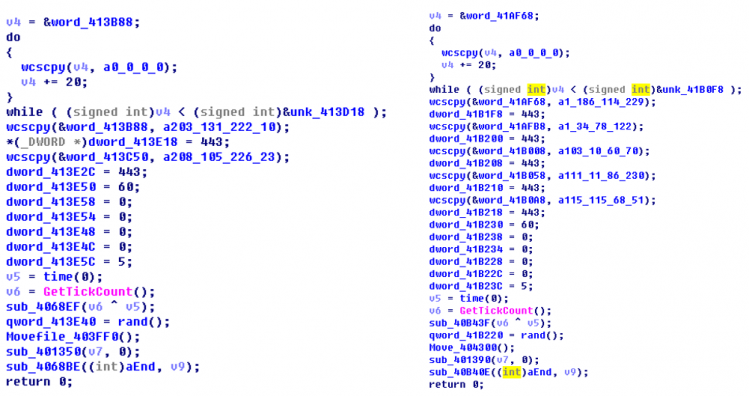
Code similarities between malware used in South Korea and in the Sony Pictures Entertainment hack.
Minseok’s paper isn’t the only one focusing on the Lazarus Group.
ESET
researchers Peter Kalnai and Michal Poslusny will present a
paper
in which they also look at the code and toolset used by the group and conclude that in fact, the Lazarus Group consists of a number of independent, code-sharing cells.
VB2018
takes place in Montreal, QC, Canada 3-5 October 2018. The
programme
includes more than 50 talks by security researchers from around the globe, as well as a dedicated
Threat Intelligence Summit
.
Register now
to guarantee your place!
Leave a Reply