

Although some inventive (and often quite impractical) non-network-based ways to remotely control malware have been presented, most botnets use the normal Internet connection of the infected device to send information and receive commands. This inherent weakness in botnets’ infrastructures makes command and control traffic a useful avenue for analysing botnet behaviour.
Haka is an open source security-oriented language that can help researchers with this task. At
VB2016
, Benoit Ancel and Mehdi Talbi, two researchers from
Stormshield
in France, will present a
paper
on Haka.
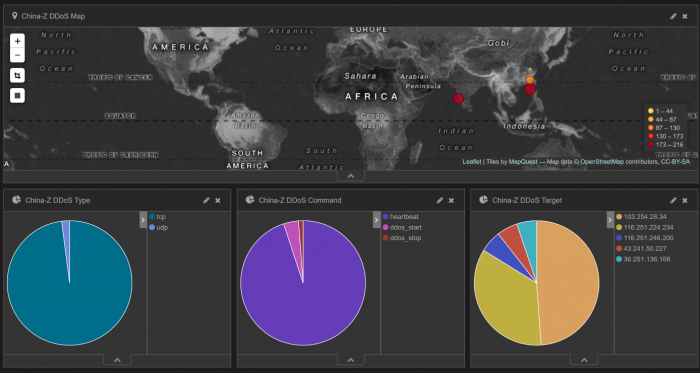
Apart from introducing the language, which looks surprisingly simple, they show how it can be used to analyse C&C traffic by way of two examples: China-Z, a DDoS botnet that uses its own protocol, and Athena, which communicates over HTTP. In the former case, they were able to show that the botnet’s targets were mainly based in Asia.
VB2016
takes place 5-7 October in Denver, Colorado. The
programme
features more than 50 talks on a wide range of security topics.
Registration
will remain open until the start of the event!

Leave a Reply