This blog post was written by Martijn Grooten and Adrian Luca.
Like every summer, millions of prospective students around the world have been taking entry exams for the university courses they want to attend. Imagine how horrible it would be if those students, after visiting the website of their university of choice, suddenly found all of their personal
files
encrypted by ransomware.
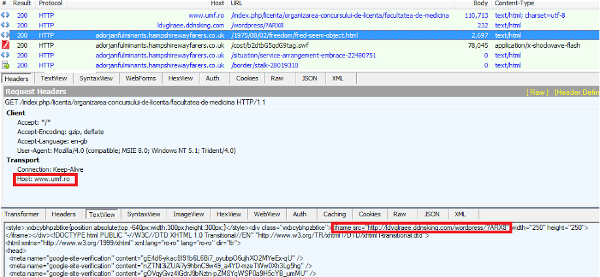
This is exactly what may have happened in Romania, as the website of the Carol Davila University of Medicine and Pharmacy (which, perhaps tellingly, has been created using Joomla) has been compromised as part of the ‘
pseudo-Darkleech
‘ campaign.
In this campaign, an iframe is inserted into the HTML code of the targeted website (hidden using CSS), into which malicious code is loaded. Following the disappearance of the Angler exploit kit last month, pseudo-Darkleech now usually serves the Neutrino exploit kit. Indeed, this is what we observed in this case.
While we did not catch the payload, it is usually the CryptXXX ransomware that is served. CryptXXX is one of the most prevalent kinds of ransomware in circulation today, and one of those which has implemented its crypto correctly – hence no decryption tools are available.
At the time of writing, hidden iframes are still being injected into the affected university’s website. We have contacted the university.
If you are interested in
keeping track of this and related campaigns,
Brad Duncan’s
malware-traffic-analysis.net
is an excellent source. Meanwhile, the
VBWeb tests
measure the ability of security products to block web-based attacks, in particular exploit kits.
Several talks at
VB2016
deal with ransomware and exploit kits, while there is also a
Small Talk
that addresses the question of how the industry can work together to stay ahead of exploit kits. (
Registration
for VB2016 is now open.)
Update
:
We have been contacted by
Malwarebytes
researcher Jérôme Segura, one of the leading experts when it comes to exploit kits, who told us that the payload in this case is in fact
CrypMIC
, which mimics CryptXXX. At VB2016, Jérôme and his colleague Chris Boyd will
present a paper
on malvertising, one of the most common ways for exploit kits to spread.
Leave a Reply