Aryeh Goretsky gives advice on how to adapt to Windows 10’s patching strategy.
Patching is hard, especially when the code base is old and the bugs are buried deeply. This was highlighted once again this week when
Microsoft
released a patch for a vulnerability that was thought to have been patched almost five years ago, but which could still be exploited.
In fact, six out of the last eight Patch Tuesdays have included patches that have caused problems for some
Windows
users.
Probably in response to this reality,
Microsoft
has announced a slightly different approach to patching for its upcoming
Windows 10
operating systems. The changes include a new Long Term Servicing (LTS) branch, as well as the use of ‘fast’ and ‘slow’ release cycles.
Today, we publish an article by
ESET
researcher Aryeh Goretsky, who takes a close look at these changes and their consequences for
Windows 10
users. He also gives some recommendations on how to adapt to this new patching strategy.
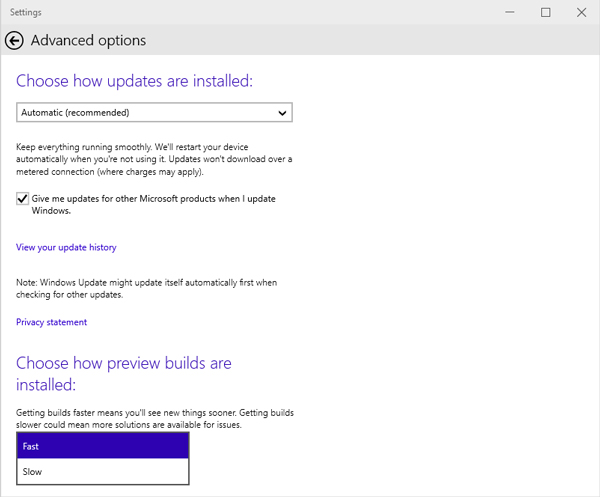
Windows 10 Enterprise Technical Preview Build 9926 showing ‘fast’ and ‘slow’ release channels.
You can read the paper
here
in HTML format or
here
as a PDF. Remember that all content published by
Virus Bulletin
can be read free of charge, with no registration required.
Have you looked at the (in?)security of Windows 10? Why not
submit an abstract
for VB2015? The call for papers closes tomorrow (13th March).
Posted on 12 March 2015 by
Martijn Grooten
Leave a Reply