Gregory Panakkal explains that there are different ways of looking at APK files – and that sometimes that can have unintended consequences.
Since the close of the VB2014 conference in Seattle in October, we have been sharing VB2014 conference papers as well as video recordings of the presentations. Today, we have added ‘Leaving our ZIP undone: how to abuse ZIP to deliver malware apps’ by Gregory Panakkal (K7 Computing).
“The
Android
system uses two different implementations when processing an APK file,” Gregory Panakkal writes in his VB2014 paper. The
K7 Computing
researcher goes on to explain that during verification, it uses a Java implementation, while a C++ based implementation is used during final extraction.
This may not be bad in itself, except that the two implementations treat APK (
Android Package
) files and their underlying ZIP structure slightly differently, which has led to some pretty serious vulnerabilities.
Most prominent among these was the ‘Master Key’ vulnerability in
Android 4.3
(
Jellybean
) and earlier, which was
discovered
by researchers
Bluebox
in 2013. The vulnerability was caused by the ZIP standard allowing for two of the files contained in the archive to have the very same name. This allowed for a malicious actor to create an APK file with a valid signature, yet with an unvalidated (and thus potentially malicious) component.
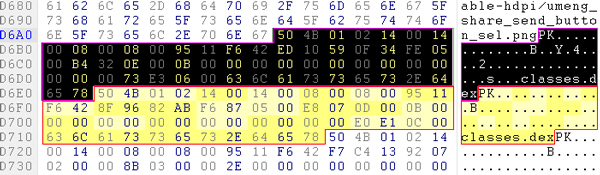
Exploiting the ‘Master Key’ vulnerability by creating two instances of classes.dex in the same APK file.
In his paper, Gregory looks at the APK format and at various weaknesses and vulnerabilities, some of which may result in anti-virus products failing to scan an APK file properly. He also demonstrated a ‘Chameleon ZIP’ file, a ZIP file that is simultaneously an
Android
APK file, a Java archive and, as an Office document, can be opened by
Open Office
.
You can read the paper
here
in HTML-format, or download it
here
as a PDF (no registration or subscription required). You can download the presentation slides
here
. We have also uploaded the presentation to our
YouTube
channel.
Have you discovered vulnerabilities in even more recent Android versions? Or have you found malicious actors exploiting such vulnerabilities? Why not
submit an abstract
for
VB2015
? The deadline for submissions is 13 March 2015.
Posted on 05 March 2015 by
Martijn Grooten
Leave a Reply