Chun Feng and Elia Florio analyse two Flash Player vulnerabilities and an IE one where Flash provides a helping hand.
Since the close of the VB2014 conference in Seattle in October, we have been sharing VB2014 conference papers as well as video recordings of the presentations. Today, we have added ‘Ubiquitous Flash, ubiquitous exploits and ubiquitous mitigation’ by Microsoft researchers Chun Feng and Elia Florio.
Last week’s
news
about a zero-day vulnerability in
Adobe
‘s
Flash Player
being used in the Angler exploit kit once again highlighted how
Flash Player
vulnerabilities affect almost every user of the Internet.
CVE-2015-0311 (which has since been
patched
;
Trend Micro
‘s Peter Pi wrote a thorough analysis
here
) wasn’t the first serious
Flash Player
vulnerability, and it won’t be the last.
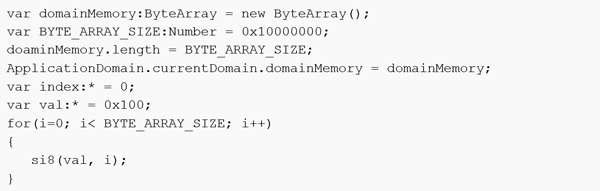
In their VB2014 paper, Chun Feng and Elia Florio look at two earlier vulnerabilities:
CVE-2013-5330
and
CVE-2014-0497
, with the latter being a consequence of the initial fix for the former not being perfect. Both vulnerabilities are caused by flaws in
Flash Player
‘s implementation of domain memory opcode and allow an attacker to craft an SWF file that can read/write to an arbitrary memory location.
The authors also look at a third vulnerability,
CVE-2014-0322
, which affects
Internet Explorer
but which is exploited with
Flash Player
used as a ‘helper’. This is possible because
IE
and the
Flash Player
plug-in share the same address space.
Finally, the paper discusses mitigation techniques
Adobe
and
Microsoft
have added against similar exploits.
You can read the paper
here
in HTML-format, or download it
here
as a PDF (no registration or subscription required).
Posted on 30 January 2015 by
Martijn Grooten
Leave a Reply