Traffic appears as requests to Google or Yandex.
There have been several recent examples of malware using a spoofed HTTP
Host
header to hide communucation with its control servers.
When a web browser sends an
HTTP
request to a web server, it includes a
Host
header, containing the host of the site that is requested. This header has been mandatory since the introduction of HTTP version 1.1 in 1999. It allows for domain-based virtual hosting, where websites on multiple domains are hosted on a single web server.
It is trivial to spoof HTTP requests and the
Host
header is no exception. This is usually of little concern: depending on the way the web server is set up, the user will get a redirect, an error, or a default website. Sites such as
Google
,
Facebook
and
Virus Bulletin
will return a
302 redirect
when a request is made for a document on a different domain, while
Microsoft
and
Yahoo
return an error. Under normal circumstances, none of this should affect the server’s security.
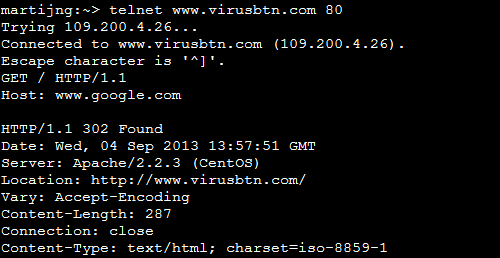
Connecting to the Virus Bulletin web server with a spoofed hostname will cause the web server to return a 302 redirect.
In some cases, using a spoofed
Host
header can be used to bypass filters that block traffic based on the content of this header. In recent months, this trick has been used by various pieces of malware.
In July,
Trend Micro
wrote
two
posts
on pieces of malware that used a spoofed
Google
header to communicate with their command and control servers. This week,
McAfee
‘s Umesh Wanve
analysed
the ‘Cidox’ trojan which sent a fake
Yandex
header, making it appear as if requests were made to the servers of the Russian search engine.
Of course, one would hope that security software would block this communication based on the IP address, or the content of the traffic. But no software is perfect and a system administrator analysing server logs could easily be deceived by the spoofed
Host
header.
In the case of big sites like
Google
and
Yandex
, a simple reverse DNS lookup on the IP address will reveal that the header is spoofed. More generally, however, it is not so simple to determine with certainty whether the host name is spoofed.
Security software and system administrators alike should thus treat the content of the
Host
header in the same way as they treat a domain name appearing in an email header: if it is known to be bad, then blocking is justified on the grounds that it is either bad, or spoofed. But if it isn’t, it shouldn’t be assumed to be valid.
Posted on 4 September 2013 by
Martijn Grooten
Leave a Reply